Common Scams and Crimes
The following are some of the most common scams and crimes that the FBI encounters, as well as tips to help prevent you from being victimized. Visit the Bureau’s White-Collar Crime and Cyber Crime webpages for information on more fraud schemes.
Advance Fee Schemes
An advance fee scheme occurs when the victim pays money to someone in anticipation of receiving something of greater value—such as a loan, contract, investment, or gift—and then receives little or nothing in return.
Advance Fee Schemes
An advance fee scheme occurs when the victim pays money to someone in anticipation of receiving something of greater value—such as a loan, contract, investment, or gift—and then receives little or nothing in return.
The variety of advance fee schemes is limited only by the imagination of the con artists who offer them. They may involve the sale of products or services, the offering of investments, lottery winnings, “found money,” or many other “opportunities.” Clever con artists will offer to find financing arrangements for their clients who pay a “finder’s fee” in advance. They require their clients to sign contracts in which they agree to pay the fee when they are introduced to the financing source. Victims often learn that they are ineligible for financing only after they have paid the “finder” according to the contract. Such agreements may be legal unless it can be shown that the “finder” never had the intention or the ability to provide financing for the victims.
Tips for Avoiding Advanced Fee Schemes:
- If the offer of an “opportunity” appears too good to be true, it probably is. Follow common business practice. For example, legitimate business is rarely conducted in cash on a street corner.
- Know who you are dealing with. If you have not heard of a person or company that you intend to do business with, learn more about them. Depending on the amount of money that you plan on spending, you may want to visit the business location, check with the Better Business Bureau, or consult with your bank, an attorney, or the police.
- Make sure you fully understand any business agreement that you enter into. If the terms are complex, have them reviewed by a competent attorney.
- Be wary of businesses that operate out of post office boxes or mail drops and do not have a street address. Also be suspicious when dealing with persons who do not have a direct telephone line and who are never in when you call, but always return your call later.
- Be wary of business deals that require you to sign nondisclosure or non-circumvention agreements that are designed to prevent you from independently verifying the bona fides of the people with whom you intend to do business. Con artists often use non-circumvention agreements to threaten their victims with civil suit if they report their losses to law enforcement.
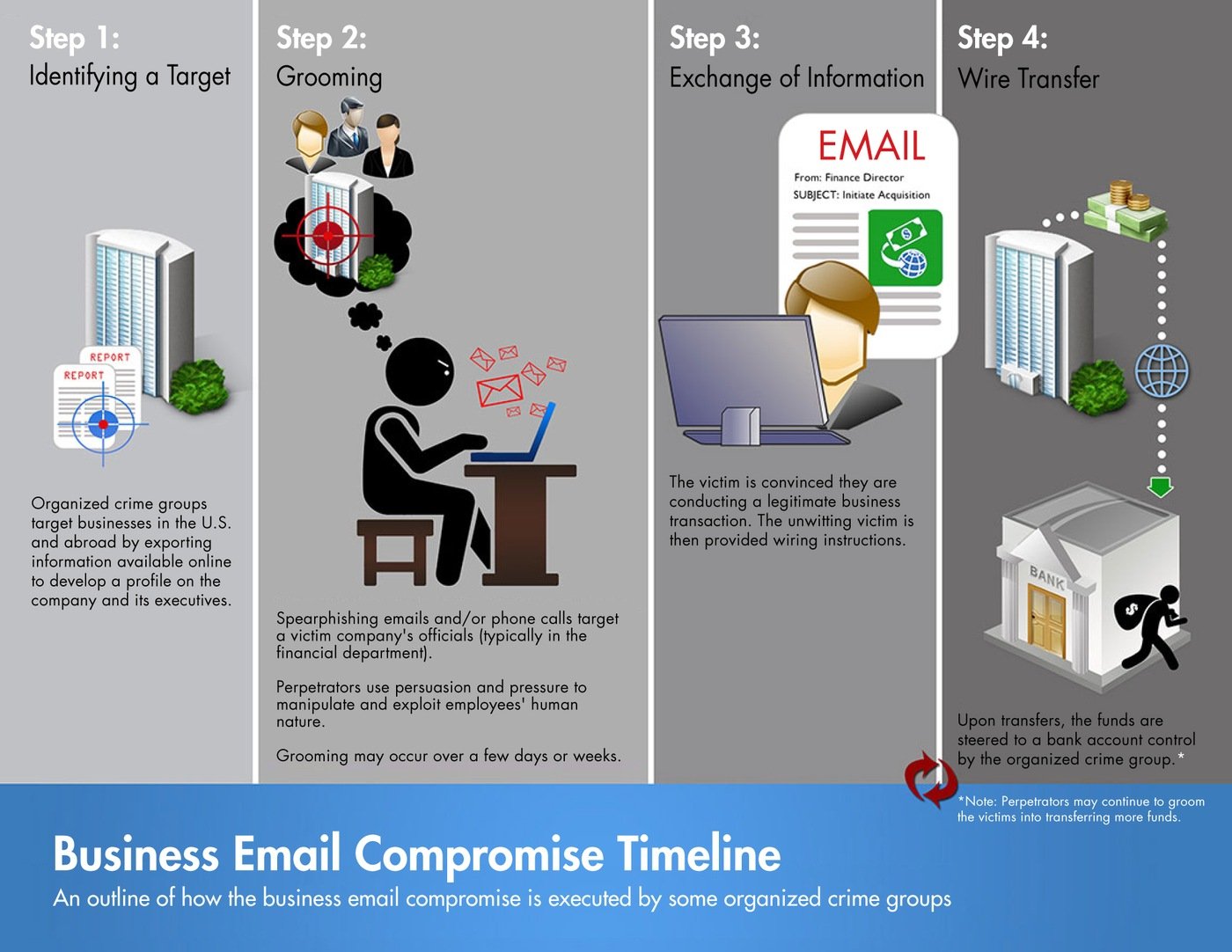
Business Email Compromise
Business email compromise (BEC) is one of the most financially damaging online crimes. It exploits the fact that so many of us rely on email to conduct business—both personal and professional.
Business email compromise (BEC)—also known as email account compromise (EAC)—is one of the most financially damaging online crimes. It exploits the fact that so many of us rely on email to conduct business—both personal and professional.
In a BEC scam, criminals send an email message that appears to come from a known source making a legitimate request, like in these examples:
- A vendor your company regularly deals with sends an invoice with an updated mailing address.
- A company CEO asks her assistant to purchase dozens of gift cards to send out as employee rewards. She asks for the serial numbers so she can email them out right away.
- A homebuyer receives a message from his title company with instructions on how to wire his down payment.
Versions of these scenarios happened to real victims. All the messages were fake. And in each case, thousands—or even hundreds of thousands—of dollars were sent to criminals instead.
How Criminals Carry Out BEC Scams
A scammer might:
- Spoof an email account or website. Slight variations on legitimate addresses (john.kelly@examplecompany.com vs. john.kelley@examplecompany.com) fool victims into thinking fake accounts are authentic.
- Send spearphishing emails. These messages look like they’re from a trusted sender to trick victims into revealing confidential information. That information lets criminals access company accounts, calendars, and data that gives them the details they need to carry out the BEC schemes.
- Use malware. Malicious software can infiltrate company networks and gain access to legitimate email threads about billing and invoices. That information is used to time requests or send messages so accountants or financial officers don’t question payment requests. Malware also lets criminals gain undetected access to a victim’s data, including passwords and financial account information.
How to Report
If you or your company fall victim to a BEC scam, it’s important to act quickly:
- Contact your financial institution immediately and request that they contact the financial institution where the transfer was sent.
- Next, contact your local FBI field office to report the crime.
- Also file a complaint with the FBI’s Internet Crime Complaint Center (IC3).
How to Protect Yourself
- Be careful with what information you share online or on social media. By openly sharing things like pet names, schools you attended, links to family members, and your birthday, you can give a scammer all the information they need to guess your password or answer your security questions.
- Don’t click on anything in an unsolicited email or text message asking you to update or verify account information. Look up the company’s phone number on your own (don’t use the one a potential scammer is providing), and call the company to ask if the request is legitimate.
- Carefully examine the email address, URL, and spelling used in any correspondence. Scammers use slight differences to trick your eye and gain your trust.
- Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
- Set up two-factor (or multi-factor) authentication on any account that allows it, and never disable it.
- Verify payment and purchase requests in person if possible or by calling the person to make sure it is legitimate. You should verify any change in account number or payment procedures with the person making the request.
- Be especially wary if the requestor is pressing you to act quickly.
Business Fraud
Business fraud consists of activities undertaken by an individual or company in a dishonest or illegal manner designed to be advantageous to the perpetrating person or establishment.
Business Fraud
Business fraud consists of dishonest and illegal activities perpetrated by individuals or companies in order to provide an advantageous financial outcome to those persons or establishments. Also known as corporate fraud, these schemes often appear under the guise of legitimate business practices. An array of crimes fall under business fraud, including the following:
- Charity fraud: Using deception to get money from individuals believing they are making donations to legitimate charity organizations, especially charities representing victims of natural disasters shortly after the incident occurs.
- Internet auction fraud: A fraudulent transaction or exchange that occurs in the context of an online auction site.
- Non-delivery of merchandise: Fraud occurring when a payment is sent but the goods and services ordered are never received.
- Non-payment of funds: Fraud occurring when goods and services are shipped or rendered but payment for them is never received.
- Overpayment scheme: An individual is sent a payment significantly higher than an owed amount and is instructed to deposit the money in their bank account and wire transfer the excess funds back to the bank of the individual or company that sent it. The sender’s bank is usually located overseas, in Eastern Europe for example, and the initial payment is found to be fraudulent, often after the wire transfer has occurred.
- Re-shipping scheme: An individual is recruited to receive merchandise at their place of residence and subsequently repackage the items for shipment, usually abroad. Unbeknownst to them, the merchandise was purchased with fraudulent credit cards, often opened in their name.
Tips for Avoiding Business Fraud:
- Purchase merchandise from reputable dealers or establishments.
- Obtain a physical address rather than simply a post office box and a telephone number, and call the seller to see if the telephone number is correct and working.
- Send an e-mail to the seller to make sure the e-mail address is active, and be wary of those that utilize free e-mail services where a credit card wasn’t required to open the account.
- Consider not purchasing from sellers who won’t provide you with this type of information.
- Purchase merchandise directly from the individual/company that holds the trademark, copyright, or patent.
Charity and Disaster Fraud
Charity and disaster fraud schemes seek donations for organizations that do little or no work. While these scams can happen at any time, they are especially prevalent after high-profile disasters.
Charity fraud schemes seek donations for organizations that do little or no work—instead, the money goes to the fake charity’s creator.
While these scams can happen at any time, they are especially prevalent after high-profile disasters. Criminals often use tragedies to exploit you and others who want to help.
Charity fraud scams can come to you in many forms: emails, social media posts, crowdfunding platforms, cold calls, etc. Always use caution and do your research when you’re looking to donate to charitable causes.
After a natural disaster or other emergency, unethical contractors and other scammers may commit insurance fraud, re-victimizing people whose homes or businesses have been damaged. Sometimes these fraudsters even pretend to be affiliated with the government, when they are not. If you need any post-disaster repairs, do your research before hiring any contractor.
Protect Yourself
The following tips can help you avoid these schemes:
- Give to established charities or groups whose work you know and trust.
- Be aware of organizations with copycat names or names similar to reputable organizations.
- Be wary of new organizations that claim to aid victims of recent high-profile disasters.
- Do your research. Use the Federal Trade Commission’s resources to examine the track record of a charity.
- Give using a check or credit card. If a charity or organization asks you to donate through cash, gift card, virtual currency, or wire transfer, it’s probably a scam. Learn more about this trick from the FTC.
- Practice good cyber hygiene:
- Don’t click links or open email attachments from someone you don’t know.
- Manually type out links instead of clicking on them.
- Don’t provide any personal information in response to an email, robocall, or robotext.
- Check the website’s address—most legitimate charity organization websites use .org, not .com.
- After a natural disaster or other emergency, carefully vet any contractors before hiring them to work on your home or business.
Counterfeit Prescription Drugs
Counterfeit prescription drugs are illegal, fake medicines that may be hazardous to your health.
Counterfeit Prescription Drugs
Counterfeit prescription drugs are illegal and may be hazardous to your health. They are fake medicines not produced to the pharmacological specifications of the drugs they claim to be. These counterfeit prescription drugs may be contaminated or contain the wrong ingredients or no active ingredient. They also could have the right active ingredient but with the wrong dosage. Don’t be fooled by fake prescription drugs masquerading as legitimate medicines, as using them may worsen your health conditions.
Tips for Avoiding Counterfeit Prescription Drugs:
- Be mindful of appearance—closely examine the packaging and lot numbers of prescription drugs and be alert to any changes from one prescription to the next.
- Consult your pharmacist or physician if your prescription drug looks suspicious.
- Alert your pharmacist and physician immediately if your medication causes adverse side effects or if your condition does not improve.
- Use caution when purchasing drugs on the Internet. Do not purchase medications from unlicensed online distributors or those who sell medications without a prescription. Reputable online pharmacies will have a seal of approval called the Verified Internet Pharmacy Practice Site (VIPPS), provided by the Association of Boards of Pharmacy in the United States.
- Be aware that product promotions or cost reductions and other “special deals” may be associated with counterfeit product promotion.
Credit Card Fraud
Credit card fraud is the unauthorized use of a credit or debit card, or card number, to fraudulently obtain money or property.
Credit Card Fraud
Credit card fraud is the unauthorized use of a credit or debit card, or similar payment tool (ACH, EFT, recurring charge, etc.), to fraudulently obtain money or property. Credit and debit card numbers can be stolen from unsecured websites or can be obtained in an identity theft scheme. Visit the FBI’s Identity Theft webpage for additional information.
Tips for Avoiding Credit Card Fraud:
- Don’t give out your credit card number online unless the site is secure and reputable. Sometimes a tiny icon of a padlock appears to symbolize a higher level of security to transmit data. This icon is not a guarantee of a secure site, but provides some assurance.
- Don’t trust a site just because it claims to be secure.
- Before using the site, check out the security/encryption software it uses.
- Make sure you are purchasing merchandise from a reputable source.
- Do your homework on the individual or company to ensure that they are legitimate.
- Obtain a physical address rather than simply a post office box and a telephone number, and call the seller to see if the telephone number is correct and working.
- Send an e-mail to the seller to make sure the e-mail address is active, and be wary of those that utilize free e-mail services where a credit card wasn’t required to open the account.
- Consider not purchasing from sellers who won’t provide you with this type of information.
- Check with the Better Business Bureau from the seller’s area.
- Check out other websites regarding this person/company.
- Don’t judge a person or company by their website; flashy websites can be set up quickly.
- Be cautious when responding to special investment offers, especially through unsolicited e-mail.
- Be cautious when dealing with individuals/companies from outside your own country.
- If possible, purchase items online using your credit card. You can often dispute the charges if something goes wrong.
- Make sure the transaction is secure when you electronically send your credit card number.
- Keep a list of all your credit cards and account information along with the card issuer’s contact information. If anything looks suspicious or you lose your credit card(s), contact the card issuer immediately.
Elder Fraud
Elder Fraud
Each year, millions of elderly Americans fall victim to some type of financial fraud or confidence scheme, including romance, lottery, and sweepstakes scams, to name a few. Criminals will gain their targets’ trust and may communicate with them directly via computer, phone, and the mail; or indirectly through the TV and radio. Once successful, scammers are likely to keep a scheme going because of the prospect of significant financial gain.
Seniors are often targeted because they tend to be trusting and polite. They also usually have financial savings, own a home, and have good credit—all of which make them attractive to scammers.
Additionally, seniors may be less inclined to report fraud because they don’t know how, or they may be too ashamed at having been scammed. They might also be concerned that their relatives will lose confidence in their abilities to manage their own financial affairs. And when an elderly victim does report a crime, they may be unable to supply detailed information to investigators.
With the elderly population growing and seniors racking up more than $3 billion in losses annually, elder fraud is likely to be a growing problem.
If you believe you or someone you know may have been a victim of elder fraud, contact your local FBI field office or submit a tip online. You can also file a complaint with the FBI’s Internet Crime Complaint Center.
- Romance scam: Criminals pose as interested romantic partners on social media or dating websites to capitalize on their elderly victims’ desire to find companions.
- Tech support scam: Criminals pose as technology support representatives and offer to fix non-existent computer issues. The scammers gain remote access to victims’ devices and sensitive information.
- Grandparent scam: Criminals pose as a relative—usually a child or grandchild—claiming to be in immediate financial need.
- Government impersonation scam: Criminals pose as government employees and threaten to arrest or prosecute victims unless they agree to provide funds or other payments.
- Sweepstakes/charity/lottery scam: Criminals claim to work for legitimate charitable organizations to gain victims’ trust. Or they claim their targets have won a foreign lottery or sweepstake, which they can collect for a “fee.”
- Home repair scam: Criminals appear in person and charge homeowners in advance for home improvement services that they never provide.
- TV/radio scam: Criminals target potential victims using illegitimate advertisements about legitimate services, such as reverse mortgages or credit repair.
- Family/caregiver scam: Relatives or acquaintances of the elderly victims take advantage of them or otherwise get their money.
- Recognize scam attempts and end all communication with the perpetrator.
- Search online for the contact information (name, email, phone number, addresses) and the proposed offer. Other people have likely posted information online about individuals and businesses trying to run scams.
- Resist the pressure to act quickly. Scammers create a sense of urgency to produce fear and lure victims into immediate action. Call the police immediately if you feel there is a danger to yourself or a loved one.
- Be cautious of unsolicited phone calls, mailings, and door-to-door services offers.
- Never give or send any personally identifiable information, money, jewelry, gift cards, checks, or wire information to unverified people or businesses.
- Make sure all computer anti-virus and security software and malware protections are up to date. Use reputable anti-virus software and firewalls.
- Disconnect from the internet and shut down your device if you see a pop-up message or locked screen. Pop-ups are regularly used by perpetrators to spread malicious software. Enable pop-up blockers to avoid accidentally clicking on a pop-up.
- Be careful what you download. Never open an email attachment from someone you don’t know, and be wary of email attachments forwarded to you.
- Take precautions to protect your identity if a criminal gains access to your device or account. Immediately contact your financial institutions to place protections on your accounts, and monitor your accounts and personal information for suspicious activity.
Each year, millions of elderly Americans fall victim to some type of financial fraud or confidence scheme, including romance, lottery, and sweepstakes scams, to name a few.
Election Crimes and Security
Fair elections are the foundation of our democracy, and the FBI is committed to protecting the rights of all Americans to vote. If you suspect a federal election crime, contact the FBI.
Fair elections are the foundation of our democracy, and the FBI is committed to protecting the rights of all Americans to vote.
The U.S. government only works when legal votes are counted and when campaigns follow the law. When the legitimacy of elections is corrupted, our democracy is threatened.
While individual states run elections, the FBI plays an important role in protecting federal interests and preventing violations of your constitutional rights.
An election crime is generally a federal crime if:
- The ballot includes one or more federal candidates
- An election or polling place official abuses their office
- The conduct involves false voter registration
- The crime intentionally targets minority protected classes
- The activity violates federal campaign finance laws
Protect Your Vote
- Know when, where, and how you will vote.
- Seek out election information from trustworthy sources, verify who produced the content, and consider their intent.
- Report potential election crimes—such as disinformation about the manner, time, or place of voting—to the FBI.
- If appropriate, make use of in-platform tools offered by social media companies for reporting suspicious posts that appear to be spreading false or inconsistent information about voting and elections.
- Research individuals and entities to whom you are making political donations.
Voter Suppression
Intentionally deceiving qualified voters to prevent them from voting is voter suppression—and it is a federal crime.
There are many reputable places you can find your polling location and registration information, including eac.gov and usa.gov/how-to-vote. However, not all publicly available voting information is accurate, and some is deliberately designed to deceive you to keep you from voting.
Bad actors use various methods to spread disinformation about voting, such as social media platforms, texting, or peer-to-peer messaging applications on smartphones. They may provide misleading information about the time, manner, or place of voting. This can include inaccurate election dates or false claims about voting qualifications or methods, such as false information suggesting that one may vote by text, which is not allowed in any jurisdiction.
- For general elections, Election Day is always the first Tuesday after November 1.
- While there are some exceptions for military overseas using absentee ballots by email or fax, you cannot vote online or by text on Election Day.
Always consider the source of voting information. Ask yourself, “Can I trust this information?” Look for official notices from election offices and verify the information you found is accurate.
Help defend the right to vote by reporting any suspected instances of voter suppression—especially those received through a private communication channel like texting—to your local FBI field office or at tips.fbi.gov.
Fraudulent Cosmetics and “Anti-Aging” Products
The Internet has given consumers widespread access to health and beauty products, including “anti-aging” products, that they do not know are fake.
Fraudulent Cosmetics and “Anti-Aging” Products
The volume of counterfeit cosmetics arriving in the U.S. is on the rise. The Internet has given consumers widespread access to health and beauty products—some labeled with “anti-aging” properties—that they don’t know are fake. Counterfeiters of personal care products increasingly view dealing in these fake items as a low-risk crime since many of them are located outside the U.S.
Government and industry studies and testing have discovered dangerous ingredients within counterfeit “anti-aging” products. Fraudulent cosmetics may contain arsenic, beryllium, and cadmium—all known carcinogens—along with high levels of aluminum and dangerous levels of bacteria from sources such as urine. Some of these products have caused conditions like acne, psoriasis, rashes, and eye infections.
Tips for Avoiding Fraudulent “Anti-Aging” Products:
- If it sounds too good to be true, it probably is. Watch out for “secret formulas” or “breakthroughs.”
- Don’t be afraid to ask questions about the product—find out exactly what it should and should not do for you.
- Research a product thoroughly before buying it. Call the Better Business Bureau to find out if other people have complained about the product.
- Be wary of products that claim to cure a wide variety of illnesses—particularly serious ones—that don’t appear to be related.
- Be aware that testimonials and/or celebrity endorsements are often misleading.
- Be very careful of products that are marketed as having no side effects.
- Question products that are advertised as making visits to a physician unnecessary.
- Always consult your doctor before taking any dietary or nutritional supplement.
Funeral and Cemetery Fraud
Regulations for prepaid funeral services vary from state to state, providing a window of opportunity for unscrupulous operators to overcharge expenses and list themselves as beneficiaries.
Funeral and Cemetery Fraud
Millions of Americans enter into contracts to prearrange their funerals and prepay some or all of the expenses involved, to ease the financial and emotional burdens on their families. Laws in individual states regulate the industry, and various states have laws to help ensure that these advance payments are available when they are needed. However, protections vary widely from state to state, sometimes providing a window of opportunity for unscrupulous operators to overcharge expenses and list themselves as financial beneficiaries.
Tips for Avoiding Funeral and Cemetery Fraud:
- Be an informed consumer. Take time to call and shop around before making a purchase. Take a friend with you who may offer some perspective to help make difficult decisions. Funeral homes are required to provide detailed general price lists over the telephone or in writing.
- Educate yourself fully about caskets before you buy one, and understand that caskets are not required for direct cremations.
- Understand the difference between funeral home basic fees for professional services and any fees for additional services.
- Know that embalming rules are governed by state law and that embalming is not legally required for direct cremations.
- Carefully read all contracts and purchasing agreements before signing, and make certain that all of your requirements have been put in writing.
- Make sure you understand all contract cancellation and refund terms, as well as your portability options for transferring your contract to other funeral homes.
- Before you consider prepaying, make sure you are well informed. When you do make a plan for yourself, share your specific wishes with those close to you.
- As a general rule governing all of your interactions as a consumer, do not allow yourself to be pressured into making purchases, signing contracts, or committing funds. These decisions are yours and yours alone.
Health Care Fraud
Health care fraud is not a victimless crime. It affects everyone causes tens of billions of dollars in losses each year. The FBI is the primary agency for investigating health care fraud, for both federal and private insurance programs.
Health care fraud is not a victimless crime. It affects everyone—individuals and businesses alike—and causes tens of billions of dollars in losses each year. It can raise health insurance premiums, expose you to unnecessary medical procedures, and increase taxes.
Health care fraud can be committed by medical providers, patients, and others who intentionally deceive the health care system to receive unlawful benefits or payments.
The FBI is the primary agency for investigating health care fraud, for both federal and private insurance programs.
The FBI investigates these crimes in partnership with:
- Federal, state, and local agencies
- Healthcare Fraud Prevention Partnership
- Insurance groups such as the National Health Care Anti-Fraud Association, the National Insurance Crime Bureau, and insurance investigative units
Tips for Avoiding Health Care Fraud
- Protect your health insurance information. Treat it like a credit card. Don’t give it to others to use, and be mindful when using it at the doctor’s office or pharmacy.
- Beware of “free” services. If you’re asked to provide your health insurance information for a “free” service, the service is probably not free and could be fraudulently charged to your insurance company.
- Check your explanation of benefits (EOB) regularly. Make sure the dates, locations, and services billed match what you actually received. If there’s a concern, contact your health insurance provider.
Common Types of Health Care Fraud
Fraud Committed by Medical Providers
- Double billing: Submitting multiple claims for the same service
- Phantom billing: Billing for a service visit or supplies the patient never received
- Unbundling: Submitting multiple bills for the same service
- Upcoding: Billing for a more expensive service than the patient actually received
Fraud Committed by Patients and Other Individuals
- Bogus marketing: Convincing people to provide their health insurance identification number and other personal information to bill for non-rendered services, steal their identity, or enroll them in a fake benefit plan
- Identity theft/identity swapping: Using another person’s health insurance or allowing another person to use your insurance
- Impersonating a health care professional: Providing or billing for health services or equipment without a license
Fraud Involving Prescriptions
- Forgery: Creating or using forged prescriptions
- Diversion: Diverting legal prescriptions for illegal uses, such as selling your prescription medication
- Doctor shopping: Visiting multiple providers to get prescriptions for controlled substances or getting prescriptions from medical offices that engage in unethical practices
Prescription Medication Abuse
Creating or using forged prescriptions is a crime, and prescription fraud comes at an enormous cost to physicians, hospitals, insurers, and taxpayers. But the greatest cost is a human one—tens of thousands of lives are lost to addiction each year. Protect yourself and your loved ones by following this guidance:
- If you are taking opioids, take them exactly as prescribed by your doctor, ideally, for the shortest amount of time possible.
- Never share your medication with others.
- Explore non-opioid options with your doctor.
- Learn more about the risks of opioid use from the CDC.
- If you have unused or expired pain medications, take them to a DEA-approved take back site for disposal.
Identity Theft
Identity theft occurs when someone assumes your identity to perform a fraud or other criminal act.
Identity Theft
Identity theft occurs when someone uses your identity in a crime or fraudulent act. It can happen to anyone—but there are steps you can take to protect yourself and to recover if it happens to you.
Learn more about identity theft from the Federal Trade Commission. If your information was stolen in a data breach, visit identitytheft.gov/databreach for specific steps to take.
Protect Yourself
- Read your credit card and bank statements each month.
- Never give your credit card number over the phone, unless you made the call and trust the business or person.
- Report suspicious transactions to your credit card company or bank.
- Review a copy of your credit report at least once each year. Notify the credit bureau in writing of any questionable entries.
- Shred any documents with personal or financial information on them.
Internet Auction Fraud
Consumers are strongly cautioned against entering into Internet auction transactions with subjects exhibiting irregular behavior or making odd payment requests.
Internet Auction Fraud
Internet auction fraud involves schemes attributable to the misrepresentation of a product advertised for sale through an Internet auction site or the non-delivery of products purchased through an Internet auction site. In advance of making a purchase on an Internet auction site, be sure to review the site’s fraud prevention tips and additional security alerts.
Tips for Avoiding Internet Auction Fraud:
- Understand as much as possible about how the auction works, what your obligations are as a buyer, and what the seller’s obligations are before you bid.
- Find out what actions the website/company takes if a problem occurs and consider insuring the transaction and shipment.
- Learn as much as possible about the seller, especially if the only information you have is an e-mail address. If it is a business, check the Better Business Bureau where the seller/business is located.
- Examine the feedback on the seller.
- Determine what method of payment the seller is asking from the buyer and where he/she is asking to send payment.
- If possible, purchase items online using your credit card, because you can often dispute the charges if something goes wrong.
- Be cautious when dealing with sellers outside the United States. If a problem occurs with the auction transaction, it could be much more difficult to rectify.
- Ask the seller about when delivery can be expected and whether the merchandise is covered by a warranty or can be exchanged if there is a problem.
- Make sure there are no unexpected costs, including whether shipping and handling is included in the auction price.
- There should be no reason to give out your social security number or driver’s license number to the seller.
Internet Fraud
Internet fraud is the use of Internet services or software with Internet access to defraud victims or to otherwise take advantage of them.
Internet Fraud
Internet fraud is the use of Internet services or software with Internet access to defraud victims or to otherwise take advantage of them. Internet crime schemes steal millions of dollars each year from victims and continue to plague the Internet through various methods. Several high-profile methods include the following:
- Business E-Mail Compromise (BEC): A sophisticated scam targeting businesses working with foreign suppliers and companies that regularly perform wire transfer payments. The scam is carried out by compromising legitimate business e-mail accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.
- Data Breach: A leak or spill of data which is released from a secure location to an untrusted environment. Data breaches can occur at the personal and corporate levels and involve sensitive, protected, or confidential information that is copied, transmitted, viewed, stolen, or used by an individual unauthorized to do so.
- Denial of Service: An interruption of an authorized user’s access to any system or network, typically one caused with malicious intent.
- E-Mail Account Compromise (EAC): Similar to BEC, this scam targets the general public and professionals associated with, but not limited to, financial and lending institutions, real estate companies, and law firms. Perpetrators of EAC use compromised e-mails to request payments to fraudulent locations.
- Malware/Scareware: Malicious software that is intended to damage or disable computers and computer systems. Sometimes scare tactics are used by the perpetrators to solicit funds from victims.
- Phishing/Spoofing: Both terms deal with forged or faked electronic documents. Spoofing generally refers to the dissemination of e-mail which is forged to appear as though it was sent by someone other than the actual source. Phishing, also referred to as vishing, smishing, or pharming, is often used in conjunction with a spoofed e-mail. It is the act of sending an e-mail falsely claiming to be an established legitimate business in an attempt to deceive the unsuspecting recipient into divulging personal, sensitive information such as passwords, credit card numbers, and bank account information after directing the user to visit a specified website. The website, however, is not genuine and was set up only as an attempt to steal the user’s information.
- Ransomware: A form of malware targeting both human and technical weaknesses in organizations and individual networks in an effort to deny the availability of critical data and/or systems. Ransomware is frequently delivered through spear phishing emails to end users, resulting in the rapid encryption of sensitive files on a corporate network. When the victim organization determines they are no longer able to access their data, the cyber perpetrator demands the payment of a ransom, typically in virtual currency such as Bitcoin, at which time the actor will purportedly provide an avenue to the victim to regain access to their data.
Investment Fraud
Investment fraud is an offer using false or fraudulent claims to solicit investments or loans, or providing for the purchase, use, or trade of forged or counterfeit securities.
Investment Fraud
Investment fraud involves the illegal sale or purported sale of financial instruments. The typical investment fraud schemes are characterized by offers of low- or no-risk investments, guaranteed returns, overly-consistent returns, complex strategies, or unregistered securities. Examples of investment fraud include advance fee fraud, Ponzi schemes, pyramid schemes, and market manipulation fraud.
These schemes often seek to victimize affinity groups—such as groups with a common religion or ethnicity—to utilize the common interests to build trust to effectively operate the investment fraud against them. The perpetrators range from professional investment advisers to persons trusted and interacted with daily, such as a neighbor or sports coach. The fraudster’s ability to foster trust makes these schemes so successful. Investors should use scrutiny and gather as much information as possible before entering into any new investment opportunities. Visit the FBI’s White-Collar Crime webpage for additional information.
Tips for Avoiding Investment Fraud:
- Don’t judge a person or company by their website; flashy websites can be set up quickly.
- Don’t invest in anything you are not absolutely sure about. Do your homework on the investment and the company to ensure that they are legitimate.
- Check out other websites regarding this person/company.
- Be cautious when responding to special investment offers, especially through unsolicited e-mail.
- Be cautious when dealing with individuals/companies from outside your own country.
- Inquire about all the terms and conditions.
Letter of Credit Fraud
Letters of credit frauds are often attempted against banks by providing false documentation to show that goods were shipped when, in fact, no goods or inferior goods were shipped.
Market Manipulation (“Pump and Dump”) Fraud
This scheme—commonly referred to as a “pump and dump”—creates artificial buying pressure for a targeted security, generally a low-trading volume issuer in the over-the-counter securities market largely controlled by the fraud perpetrators.
Money Mules
A money mule is someone who transfers or moves illegally acquired money on behalf of someone else. Some money mules know they are supporting criminal enterprises; others are unaware that they are helping criminals profit. Don’t be a mule.
Nigerian Letter or “419” Fraud
Nigerian letter frauds combine the threat of impersonation fraud with a variation of an advance fee scheme in which a letter mailed, or e-mailed, from Nigeria offers the recipient the “opportunity” to share in a percentage of millions of dollars that the author—a self-proclaimed government official—is trying to transfer illegally out of Nigeria.
Non-Delivery of Merchandise
Non-delivery of merchandise is a scheme most often linked to Internet auction fraud, but also can be considered a form of business fraud in certain cases.
Online Vehicle Sale Fraud
The FBI warns consumers that criminal perpetrators may post fraudulent online classified advertisements offering vehicles for sale that are not, nor have ever been, in their possession.
Ponzi Schemes
“Ponzi” schemes promise high financial returns or dividends not available through traditional investments. Instead of investing the funds of victims, however, the con artist pays “dividends” to initial investors using the funds of subsequent investors.
Prime Bank Note Fraud
The purpose of these frauds is generally to encourage the victim to send money to a foreign bank, where it is eventually transferred to an off-shore account in the control of the con artist. From there, the victim’s money is used for the perpetrator’s personal expenses or is laundered in an effort to make it disappear.
Pyramid Schemes
As in Ponzi schemes, the money collected from newer victims of pyramid schemes is paid to earlier victims to provide a veneer of legitimacy. In pyramid schemes, however, the victims themselves are induced to recruit further victims through the payment of recruitment commissions.
Ransomware
Ransomware is a type of malicious software, or malware, that prevents you from accessing your computer files, systems, or networks and demands you pay a ransom for their return.
Redemption / Strawman / Bond Fraud
This scheme predominately uses fraudulent financial documents—often referred to as “bills of exchange,” “promissory bonds,” “indemnity bonds,” “offset bonds,” “sight drafts,” or “comptrollers warrants”—that appear to be legitimate.
Reverse Mortgage Scams
Reverse mortgage scams are engineered by unscrupulous professionals in a multitude of real estate, financial services, and related companies to steal the equity from the property of unsuspecting senior citizens or to use these seniors to unwittingly aid the fraudsters in stealing equity from a flipped property.
Romance Scams
Romance scams occur when a criminal adopts a fake online identity to gain a victim’s affection and trust. The scammer then uses the illusion of a romantic or close relationship to manipulate and/or steal from the victim.
Sextortion
Sextortion is a crime that involves adults coercing kids and teens into sending explicit images online. The FBI has several resources to help caregivers and young people better understand what sextortion is, how to protect against it, and how to talk about this growing and devastating threat.
Skimming
Skimming occurs when devices illegally installed on ATMs, point-of-sale (POS) terminals, or fuel pumps capture data or record cardholders’ PINs.