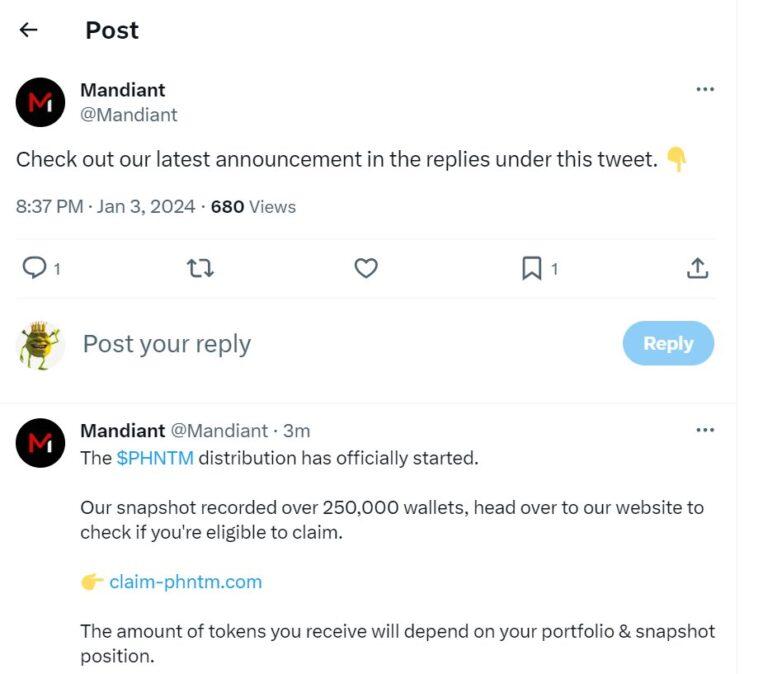
Hackers Flood Dark Web Markets With Hijacked X (Twitter) Gold accounts
In the age of social media, verification badges hold significant power.
On Twitter, the coveted blue tick (now replaced with “Gold”) signifies legitimacy and influence, commanding increased trust and engagement from followers.
However, with the platform’s recent monetization of verification, a disturbing trend has emerged: CloudSEK unmasks a nefarious scheme: Compromised Twitter Gold accounts for sale on the dark web
The Rise of Twitter Gold on the Dark Web:
Since December 2022, Twitter has offered paid verification through its “Twitter Gold” subscription.
This move opened a loophole for cybercriminals, who exploit various methods to acquire and sell verified accounts on the dark web.
These accounts, advertised on forums and Telegram channels, typically fall into three categories:
Fresh accounts with bought verification: These accounts are newly created and quickly verified through paid subscriptions. They often lack followers and activity, making them ideal for impersonation scams.
Brute-forced existing accounts: Hackers use automated tools to crack passwords and gain access to dormant accounts. Once hijacked, these accounts are verified and sold, offering a seemingly legitimate online persona.
Information stealer malware:
Malware infects devices, stealing login credentials for social media accounts.
Criminals then filter these stolen accounts, identifying and verifying valuable Twitter profiles for resale.
The motivations behind buying Twitter Gold accounts on the dark web are vast:
Phishing and scams: Verified accounts appear trustworthy, making them ideal tools for phishing attacks, spreading misinformation, and tricking users into revealing personal information.
Brand impersonation: Impersonating reputable brands or individuals allows scammers to leverage established trust for fraudulent activities.
Cryptocurrency theft: Verified accounts can be used to promote fake cryptocurrency giveaways or pump-and-dump schemes, ultimately stealing from unsuspecting users.
Reputation damage: Compromised accounts can be used to spread damaging content about individuals or organizations, causing reputational harm.
Identifying and Mitigating the Threat:
Organizations and individuals can take proactive steps to protect themselves from Twitter Gold scams:
Implement strong password hygiene: Encourage using unique, complex passwords and enable multi-factor authentication.
Monitor online activity: Regularly review social media accounts for suspicious activity, such as unauthorized login attempts or changes to account details.
Be wary of unsolicited messages: Verify the legitimacy of any message or link received from a verified account, especially if it seems too good to be true.
Report suspicious activity: Report any suspicious activity to Twitter and relevant authorities.
The post Hackers Flood Dark Web Markets With Hijacked X (Twitter) Gold accounts appeared first on Cyber Security News.